You have the right strategies, you have the right people and processes. Now it’s time to implement third-party risk management efficiently, because no one wants added cost pressures.
With so much data being created and passed around, traditional or manual practices are no longer suited to the new reality of sheer information volume and scale.
As there is no one-size-fits-all solution, organisations have started to configure their technology stack to support third-party risk management programs across different business functions – while ensuring shared visibility.
Why technology for enterprise vendor risk management?
Before diving deeper into the specific ways in which technology can help, it is useful to consider the high-level benefits to set the right level of expectations for technology adoption. Many of the benefits fall under the "cost avoidance" category:
- Centralised hub of up-to-date information shared with the right stakeholders to inform decision-making
- Ensuring every possible due diligence step has been taken – shield of defence in case of an audit
- Freed up time to focus on strategic tasks that can mitigate risks much earlier such as demand planning, category management, tender documentation and specification
- Facilitating and not hindering the adoption of best practices in procurement/governance
- Enabling multiple supplier segmentation strategies and applying those to various workflows
- Ability to pinpoint where, when, who, how at any stage of the procurement lifecycle to improve accountability and proactive troubleshooting
Mapping third-party risk management solutions against risks
The following tables provide a vendor management risk / technology matrix - or how technology can help mitigate various risk areas mentioned in previous articles of this series.
With each risk topic, you’ll find a description of the risk, the consequence for not managing it, the technology solution, and the benefits.
|
|
Legal compliance |
Diversity quotas |
Exposure to fraud (external) |
|
Description |
Unethical, non-compliant practices conducted in your supply chain, intentionally or not |
Government-imposed or corporate sustainability quota requirements not met |
Unauthorised vendor profile updates |
|
Consequence |
Non-compliant organisations may face penalties or brand damage |
Missed opportunities on government contracts and revenue, brand reputation |
Payments made to imposters of the vendor |
|
Solutions |
Prequalification questionnaires, compliance document expiry notifications |
Supplier database segmentation and reporting, prequalification questionnaires |
Secure vendor portals and notifications of significant changes |
|
Benefits |
Legal compliance at scale, better vendor relationship management |
Better understanding of supplier pool to diversify sources, improved standing with clients |
Improved security and accountability |
|
|
Exposure to fraud (internal) |
Business continuity/ Overdependence |
Choosing the inappropriate vendor |
|
Description |
Conflict of interest not declared or managed properly |
Business disruption due to issues with key vendors. |
No accessible data to inform decision making during the subcontractor selection process |
|
Consequence |
Value for money not achieved and possible investigation (internal/external) |
Operational delays, financial loss, or diminishing gains from bulk buying
|
Value for money not achieved, potential delays or reputational issues |
|
Solution |
Tailored valuation and approval workflows, audit trail of procurement activities |
Up-to-date prequalified vendor database. Access to an open marketplace |
Up-to-date vendor database, evaluation & approval workflow |
|
Benefits |
Oversight of supply chain, ensuring probity |
Diversified vendor pool for competitive advantage |
Business continuity, or defensible decisions |
|
|
Failure to deliver on contract |
Spend leakage |
Inefficient tools/systems |
|
Description |
No shared visibility over contract timeline and milestones |
Lack of process governance, maverick spend, poor spend visibility |
Reliance on manual or paper-based processes, task duplication and siloed systems |
|
Consequence |
Project delays, potential financial and reputational impact |
Pressure on margins, operational delays due to cost overruns |
High administrative burden that leads to process bottlenecks and non-compliance |
|
Solution |
Contract management, post-engagement performance evaluation |
Audit trail of procurement activities, threshold protected purchasing, ERP integrations to match PO records. |
Automated workflows, customisable user access, audit trail |
|
Benefits |
Opportunities for early rectification, informed decision at next sourcing event |
Supply chain visibility and accountability |
Enabling efficiency, collaboration and governance |
Technology is not the silver bullet
As always, the caveat is technology alone does not solve the third-party vendor risk management puzzle. It helps align people and processes, thereby enabling stronger governance.
Another way to look at it is technology serves as the conduit between the lines of defence mentioned previously. Below is an example of the vendor onboarding process facilitated by technology across different stakeholders.
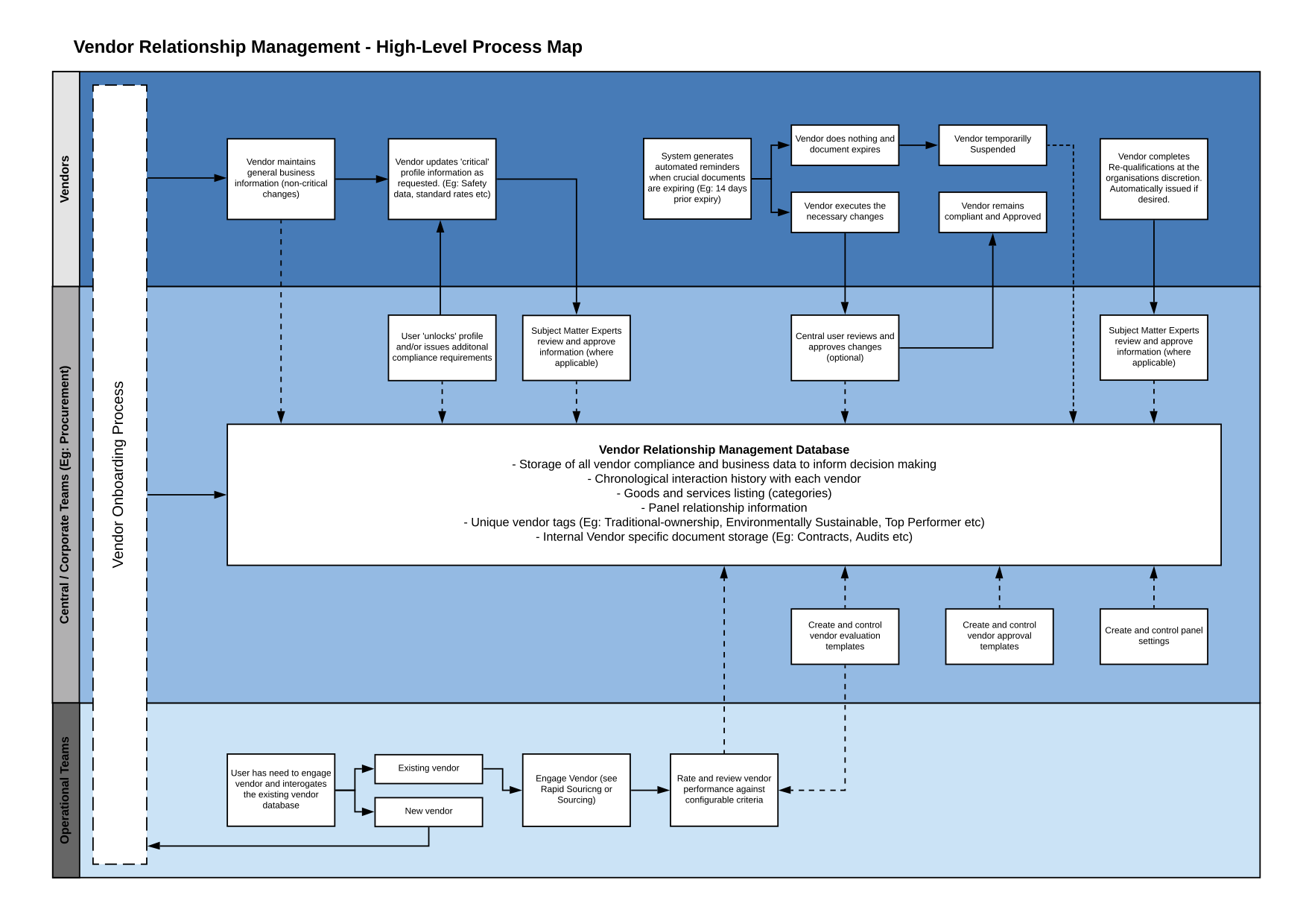
Indeed, this is the perfect-world scenario, where stakeholders at all levels are aligned on the executives’ vision around risk mitigation, processes are designed to match users’ needs, and investment into the right technology platform is made to ensure maximum uptake.
Where to from here?
Supply chain risk management is an enterprise-wide initiative that requires collaboration across traditionally siloed departments: procurement, legal, Industrial Relations, operations.
How do we move from firefighting to prevention, from reactive to proactive?
And how much budget should we allocate to supplier risk and performance management? Figures have been thrown around, such as:
“Organisations should also consider allocating a higher proportion of annual enterprise risk management operating expenditure (opex) to pre-screening and exit planning and termination activities – perhaps about 10% to each of these. This would supplement the focus on selection – due diligence and contracting at 20 to 30% of the budget, and ongoing monitoring at 50% or a little above.” (Deloite)
In short, organisations need to increase investment to match the importance of third parties in the supply chain – which is high as ever.
Our latest research report Building in the Dark - High-risk Supply Chains: Attitudes, Responses & Opportunities also touches on how industry peers are or are not using technology in managing their vendors.
If you’re interested in some benchmarking data to build a business case, download the white paper here.

Recent Articles
2025 in review: Milestones, insights and achievements
2025 – a year of that brought meaningful developments for Felix as we continue to address the evolving needs of organisations navigating complex supply-chain environments.
Top 10 reasons for a centralised vendor database
As organisations grow, so does the complexity of managing vendor relationships. Many still rely on spreadsheets or siloed systems, which can lead to inefficiencies, data inconsistencies, and compliance risks. A centralised vendor database offers a smarter, more scalable solution that brings structure, visibility, and control to procurement operations.
Here are the top 10 reasons why centralising your vendor data is a strategic move.
Five ways poor contract storage could be costing your organisation money
Contracts are the backbone of every business relationship – legally binding documents that define expectations, responsibilities, and value.
But what if the way your organisation stores those contracts is quietly costing you money?
Let's stay in touch
Get the monthly dose of supply chain, procurement and technology insights with the Felix newsletter.







